I describe a scenario when this kind of attack happens, supplying a few technical details and a solution that will help you to be protected avoiding that an attack like this comes to be successful.
Attacks always happen. This is a rule of thumb.
The golden key is to avoid them or make them ineffective, and if possible, given some extra duty for those who live by stealing your privacy.
This article was written to attend most people, no matter the technical knowledge they may have and for this reason, contains extra details.
After all, security is for all.
SCENARIO – ATTACK PRE-CONDITIONS
You are working on your notebook connected to the modem using an RJ-45 cable to access the Internet plugged straight to the router.
See figure.

The cable connecting to the notebook (or desktop)

Notice that you may have another cable connecting to a local network, or not, or whatever. It doesn’t matter.
The key to our scenario is that the Internet connection is via cable and not Wi-Fi.
If you have this, you get on the Windows taskbar the icon shown by the red arrow:
![]()
If your connection is using the Wi-Fi, the icon is different, something like this:
![]()
When you click on the network icon (red arrow), you get the following:
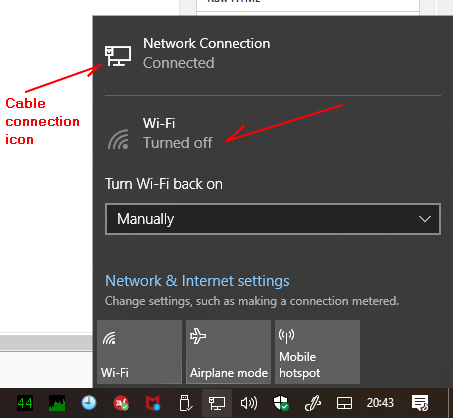
Notice that Wi-Fi is turned off, instead, the cable connection is on.
THE ATTACK
The Internet connection starts to fail and stops.
Without connection, if you are desperate, you try to connect via Wi-Fi.
This is exactly the point when the attack begins.
The Wi-Fi connection protocol sends your password at the handshake when it becomes vulnerable to be sniffed by the attacker.
It is exactly what the intruder wants you to do – switching from cable to Wi-Fi it is possible to get your password and from that point on your privacy has gone.
This YouTube video shows how a password is obtained during the handshake.
Hacking Into WPA and WPA2 Wireless Networks
There is also a good summary of complementary information here: “How to Hack WiFi (Wireless) Network“.
The key to this attack is to force you to go on Wi-Fi but this is only possible if the intruder has the means to provide this situation that depends on the flaws of the router model.
Older routers are more vulnerable, like for instance D-Link DWR-922, although excellent device, but the years have come to it…
During this attack, the cable connection is constantly put down.
After the attack is over, the device will get back to work as usual.
The intruder must be near you, or at least the devices that is handled during the attack remotely.
There are tools that warn you when suspect action is being taken on your connection and also identify from where it comes.
Lenovo offers this feature embedded on its recent machines. The figure below shows the “Threat locator” in action.
HOW TO PROTECT YOURSELF
1. Golden rule:
Avoid Wi-Fi connection for sensitive information.
Better using cable connection to the router that avoids handshake and makes it possible to detect when the thing goes wrong.
Use Wi-Fi for non-sensitive information, like watching movies, etc.
2. Use a smartphone for financial procedures (bank operations), but be aware of the next advice.
3. Make sure that your smartphone is secure.
Smartphones are strict personal devices.
Never, ever, borrow it to someone.
3b. Install good security applications.
It is required a good antivirus, firewall e a VPN service.
What is a VPN?
VPN avoids network exposure.
4. Use strong passwords.
In this kind of attack, the password strength doesn’t help.
So, strong passwords are useless?
The answer is NO.
They are required to protect you against other kinds of attacks.
HOW TO HANDLE THIS ATTACK
Just turn off the router.
If you have a second, switch to the other, otherwise, you may use your smartphone to provide a temporary connection through the “Tethering” feature until you provide a new router.
When the attack is gone, the device returns to work on cable, but the intruder may return a new attack bothering you.
Brazilian system analyst graduated by UNESA (University Estácio de Sá – Rio de Janeiro). Geek by heart.